Monitor Fleet Behavior

When you have organized your fleet into groups, you can use this feature to control your fleet. This is useful to solve problems such as mitigating security incidents or launching new features. You can also leverage Logging and Fine-grained Logging when you organize your thing using Thing Groups.
Monitoring and Applying Customized Policies on Your Fleet
Your support team reported that some of your customers are opening trouble tickets complaining about a strange behavior on their devices. Only customers in the NYC location are being impacted. You want to enable a DEBUG log level to this group and start troubleshoot the issue.
AWS IoT can send all progress events about each message as it passes from your devices through the message broker, device gateway, and the rules engine.
You can configure logging in two ways:
- Global logging
- It sets one logging level for all logs no matter what resource has triggered the logs
- Fine-grained logging.
- It allows you to set a logging level for a specific thing group.
To enable AWS IoT logging, you must create an AWS Identity and Access Management (IAM) role, register it with AWS IoT, and then configure logging on Cloudwatch.
An IAM role has already been created for you using the name IoTLogsRole-HASH. It contains the required permissions:
Role policy
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"logs:CreateLogGroup",
"logs:CreateLogStream",
"logs:PutLogEvents",
"logs:PutMetricFilter",
"logs:PutRetentionPolicy"
],
"Resource": [
"*"
]
}
]
}
Trust Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "",
"Effect": "Allow",
"Principal": {
"Service": "iot.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
Enabling Global Logging
Open the AWS IoT Console, if it is not already opened:
- Type
iot coreon the Find Services - Click on IoT Core result
 Under the IoT Home page, on the left menu:
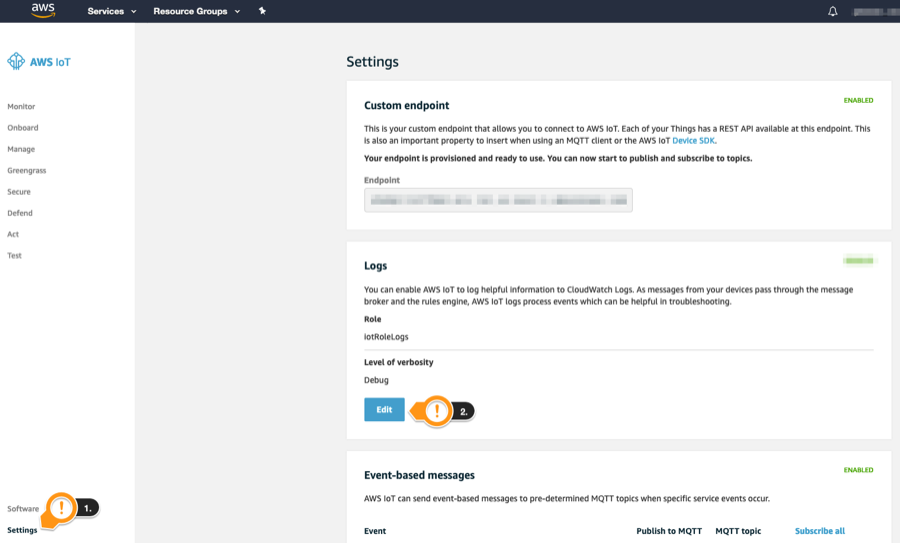
Under the IoT Home page, on the left menu: - Click Settings
- Under Logs, click Edit
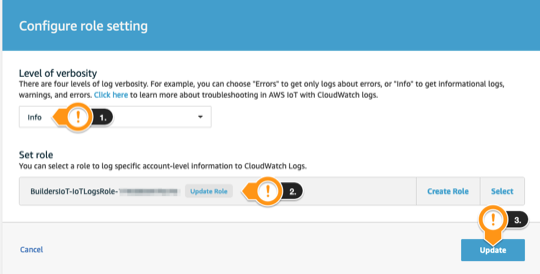
- Under Level of verbosity, choose Info
- Under Set role, choose the
<StackName>-IoTLogsRole-<HASH> - Click Update
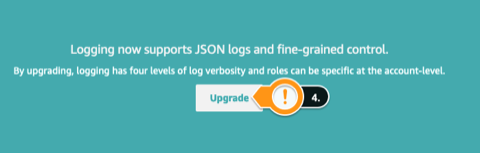
- On the green panel, click Upgrade
Enabling fine-grained logging
Still on the AWS IoT console:
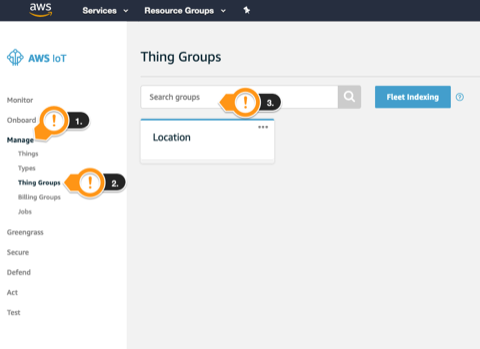
- Click Manage
- Click Thing Groups
- Click Search groups field
- Under Locate or identify specific groups, click Search
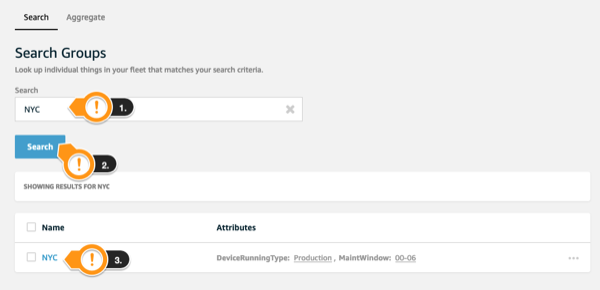
- Under Search field, type
NYC - Click Search
- Click NYC Group
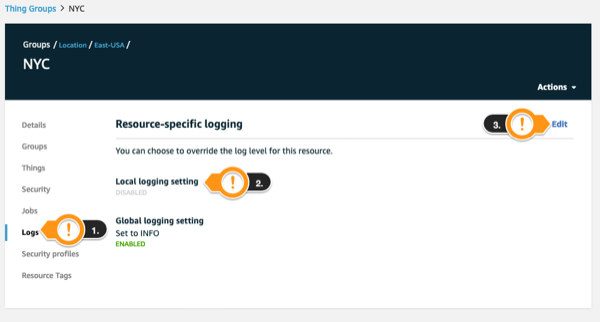
- Click Logs
- Notice Local logging setting is disabled. Only Global setting is applied place right now.
- Click Edit
- Choose Debug (most verbose) option
- Click Update
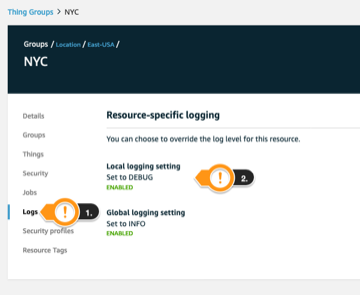
- Back in the group details page, click Logs
- Notice this group is in DEBUG mode, while the others are follow the Global level
Checking Logs (Optional)
You can use the AWS Cloudwatch console to see the AWS ioT logs.
Open the Amazon CloudWatch console, if it is not already opened:
- Type
cloudwatchon the Find Services - Click on Cloudwatch result
- Under Logs on the left side, click Log groups
- Click on AWSIotLogsV2 LogGroup on the list
- Feel free to explore the logs
Conclusion
Congratulations! You have enabled logging to monitor your fleet. You can now move to the other section.