Applying Group Permissions

You have a new request from the Marketing and Development department: They want to enable a beta feature in the SanFrancisco devices in Production to integrate an Alexa skill on smart A/C devices, that enables voice control for room temperature.
You need an additional security policy that allows the devices in the SanFrancisco location to listen to a new topic named alexa/integration/<deviceName>.
The device already has the code to process the command.
Attaching a policy to a group will allow every thing under this group or any things/groups bellow its hierarchy, to inherit the policy permissions.
Creating a new policy
In this exercise, you will use a previously created policy file, alexaPolicy.json added on your Cloud9 environment.
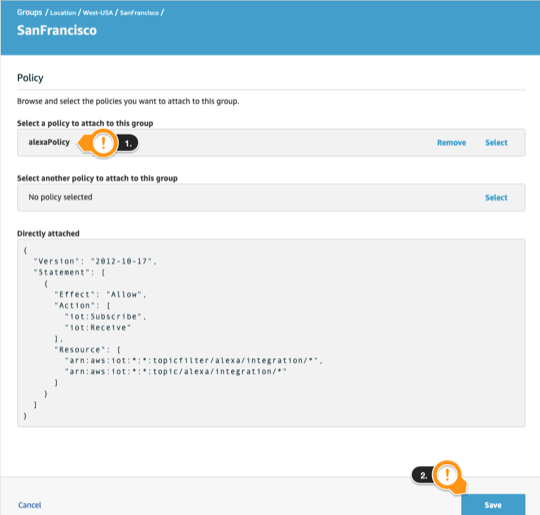
This policy allows the subscribe action to the new topic alexa/integration/<device-name>:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"iot:Subscribe",
"iot:Receive"
],
"Resource": [
"arn:aws:iot:<region>:<account>:topicfilter/alexa/integration/*",
"arn:aws:iot:<region>:<account>:topic/alexa/integration/*"
]
}
]
}
In order to process the message successfully, the policy needs to allow both Subscribe and Receive actions. Additionally, it contains a wild card (*) after the alexa/integration/ because you need to apply the same policy to every device in the group.
A very permissive policy has been used to help the flow of the task. The recommended way in production would be using a policy Variable like ${iot.Connection.Thing.ThingName} or another certificate parameter.
Go back to the Cloud9 tab opened previously:
- Make sure your are in the right directory by copy and paste the command below into the Cloud9 terminal
cd ~/environment/IoTRepository/
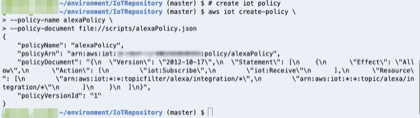
- Copy and paste the command is below into the Cloud9 terminal:
# create iot policy
aws iot create-policy \
--policy-name alexaPolicy \
--policy-document file://scripts/alexaPolicy.json
Ok! if you see this output, the command run successfully:
Attaching the policy to the thing group
Open the AWS IoT Console, if it is not already opened:
- Type
iot coreon the Find Services - Click on IoT Core result
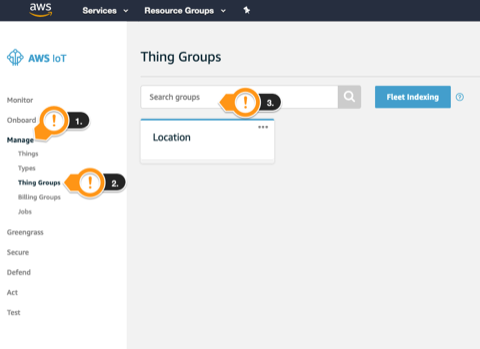
 Under the IoT Home page, on the left menu:
Under the IoT Home page, on the left menu: - Click Manage
- Click Thing Groups
- Click Search groups field
- Under Locate or identify specific groups, click Search
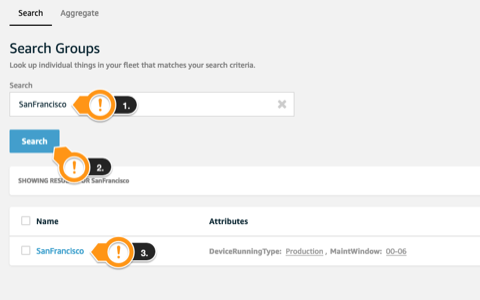
- Under Search field, type
SanFrancisco - Click Search
- Click SanFrancisco Group
- Click Security
- Click Edit
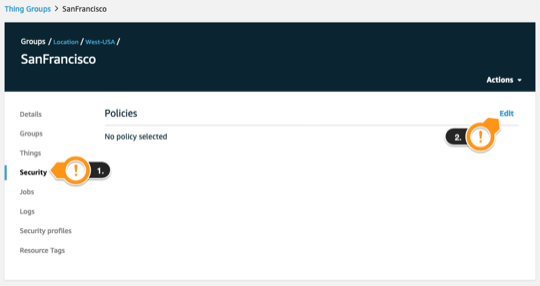
- Choose alexaPolicy policy. Click Close to select
- Click Save
Checking changes taking effect
You can use the Fleet Dashboard to get an overview of your current fleet and see the devices provisioned on your account.
- Open the Fleet Dashboard tab opened previously.
After opening the Fleet Dashboard, you see all the current devices provisioned on your account.
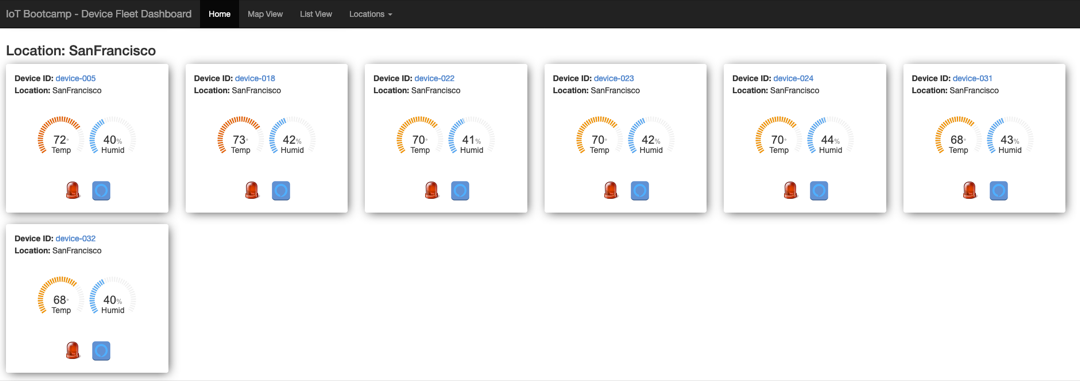
Notice that each device has the following information (in that order):
- DeviceID
- Location
- Temperature
- Humidity
- Led status
- Alexa status
Scroll down to the SanFrancisco location devices and check if the Alexa icon changed from |this:  to this:
to this:  .
.
The other locations remains with no Alexa integration, since we just applied alexaPolicy on SanFrancisco group.
Conclusion
Congratulations! You have enabled group policies. You can now move to the other section.